mirror of
https://github.com/nostr-protocol/nips.git
synced 2026-02-01 06:48:51 +00:00
Compare commits
23 Commits
nh-editabl
...
nip46-pubk
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
35f6a880f1 | ||
|
|
2838e3bd51 | ||
|
|
926a51e722 | ||
|
|
6376fd8c69 | ||
|
|
b8a5447e26 | ||
|
|
18bdc0ce8c | ||
|
|
b79e46d33c | ||
|
|
b58f02925e | ||
|
|
39154346bb | ||
|
|
29696eb364 | ||
|
|
b0840be312 | ||
|
|
690e1b065c | ||
|
|
ec8eb9af0b | ||
|
|
4c0f963292 | ||
|
|
1cb4a1f764 | ||
|
|
bff61dd310 | ||
|
|
03f3bc3967 | ||
|
|
f72a2f69ed | ||
|
|
6bcd89c097 | ||
|
|
087437042b | ||
|
|
d546936073 | ||
|
|
df977f3874 | ||
|
|
f57d559dc0 |
4
05.md
4
05.md
@@ -33,7 +33,7 @@ It will make a GET request to `https://example.com/.well-known/nostr.json?name=b
|
||||
"bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9"
|
||||
}
|
||||
}
|
||||
````
|
||||
```
|
||||
|
||||
or with the **recommended** `"relays"` attribute:
|
||||
|
||||
@@ -46,7 +46,7 @@ or with the **recommended** `"relays"` attribute:
|
||||
"b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9": [ "wss://relay.example.com", "wss://relay2.example.com" ]
|
||||
}
|
||||
}
|
||||
````
|
||||
```
|
||||
|
||||
If the pubkey matches the one given in `"names"` (as in the example above) that means the association is right and the `"nip05"` identifier is valid and can be displayed.
|
||||
|
||||
|
||||
28
11.md
28
11.md
@@ -14,6 +14,8 @@ When a relay receives an HTTP(s) request with an `Accept` header of `application
|
||||
{
|
||||
"name": <string identifying relay>,
|
||||
"description": <string with detailed information>,
|
||||
"banner": <a link to an image (e.g. in .jpg, or .png format)>,
|
||||
"icon": <a link to an icon (e.g. in .jpg, or .png format>,
|
||||
"pubkey": <administrative contact pubkey>,
|
||||
"contact": <administrative alternate contact>,
|
||||
"supported_nips": <a list of NIP numbers supported by the relay>,
|
||||
@@ -35,6 +37,21 @@ A relay may select a `name` for use in client software. This is a string, and S
|
||||
|
||||
Detailed plain-text information about the relay may be contained in the `description` string. It is recommended that this contain no markup, formatting or line breaks for word wrapping, and simply use double newline characters to separate paragraphs. There are no limitations on length.
|
||||
|
||||
### Banner
|
||||
|
||||
To make nostr relay management more user friendly, an effort should be made by relay owners to communicate with non-dev non-technical nostr end users. A banner is a visual representation of the relay. It should aim to visually communicate the brand of the relay, complementing the text `Description`. [Here is an example banner](https://image.nostr.build/232ddf6846e8aea5a61abcd70f9222ab521f711aa545b7ab02e430248fa3a249.png) mockup as visualized in Damus iOS relay view of the Damus relay.
|
||||
|
||||
### Icon
|
||||
|
||||
Icon is a compact visual representation of the relay for use in UI with limited real estate such as a nostr user's relay list view. Below is an example URL pointing to an image to be used as an icon for the relay. Recommended to be squared in shape.
|
||||
|
||||
```jsonc
|
||||
{
|
||||
"icon": "https://nostr.build/i/53866b44135a27d624e99c6165cabd76ac8f72797209700acb189fce75021f47.jpg",
|
||||
// other fields...
|
||||
}
|
||||
```
|
||||
|
||||
### Pubkey
|
||||
|
||||
An administrative contact may be listed with a `pubkey`, in the same format as Nostr events (32-byte hex for a `secp256k1` public key). If a contact is listed, this provides clients with a recommended address to send encrypted direct messages (See [NIP-17](17.md)) to a system administrator. Expected uses of this address are to report abuse or illegal content, file bug reports, or request other technical assistance.
|
||||
@@ -257,17 +274,6 @@ Relays that require payments may want to expose their fee schedules.
|
||||
}
|
||||
```
|
||||
|
||||
### Icon
|
||||
|
||||
A URL pointing to an image to be used as an icon for the relay. Recommended to be squared in shape.
|
||||
|
||||
```jsonc
|
||||
{
|
||||
"icon": "https://nostr.build/i/53866b44135a27d624e99c6165cabd76ac8f72797209700acb189fce75021f47.jpg",
|
||||
// other fields...
|
||||
}
|
||||
```
|
||||
|
||||
### Examples
|
||||
|
||||
As of 2 May 2023 the following command provided these results:
|
||||
|
||||
184
22.md
Normal file
184
22.md
Normal file
@@ -0,0 +1,184 @@
|
||||
NIP-22
|
||||
======
|
||||
|
||||
Comment
|
||||
-------
|
||||
|
||||
`draft` `optional`
|
||||
|
||||
A comment is a threading note always scoped to a root event or an `I`-tag.
|
||||
|
||||
It uses `kind:1111` with plaintext `.content` (no HTML, Markdown, or other formatting).
|
||||
|
||||
Comments MUST point to the root scope using uppercase tag names (e.g. `K`, `E`, `A` or `I`)
|
||||
and MUST point to the parent item with lowercase ones (e.g. `k`, `e`, `a` or `i`).
|
||||
|
||||
```js
|
||||
{
|
||||
kind: 1111,
|
||||
content: '<comment>',
|
||||
tags: [
|
||||
// root scope: event addresses, event ids, or I-tags.
|
||||
["<A, E, I>", "<address, id or I-value>", "<relay or web page hint>", "<root event's pubkey, if an E tag>"],
|
||||
// the root item kind
|
||||
["K", "<root kind>"],
|
||||
|
||||
// parent item: event addresses, event ids, or i-tags.
|
||||
["<a, e, i>", "<address, id or i-value>", "<relay or web page hint>", "<parent event's pubkey, if an e tag>"],
|
||||
// parent item kind
|
||||
["k", "<parent comment kind>"]
|
||||
]
|
||||
// other fields
|
||||
}
|
||||
```
|
||||
|
||||
Tags `K` and `k` MUST be present to define the event kind of the root and the parent items.
|
||||
|
||||
`I` and `i` tags create scopes for hashtags, geohashes, URLs, and other external identifiers.
|
||||
|
||||
The possible values for `i` tags – and `k` tags, when related to an extenal identity – are listed on [NIP-73](73.md).
|
||||
Their uppercase versions use the same type of values but relate to the root item instead of the parent one.
|
||||
|
||||
`q` tags MAY be used when citing events in the `.content` with [NIP-21](21.md).
|
||||
|
||||
```json
|
||||
["q", "<event-id> or <event-address>", "<relay-url>", "<pubkey-if-a-regular-event>"]
|
||||
```
|
||||
|
||||
`p` tags SHOULD be used when mentioning pubkeys in the `.content` with [NIP-21](21.md).
|
||||
If the parent item is an event, a `p` tag set to the parent event's author SHOULD be added.
|
||||
|
||||
```json
|
||||
["p", "<pubkey>", "<relay-url>"]
|
||||
```
|
||||
|
||||
## Examples
|
||||
|
||||
A comment on a blog post looks like this:
|
||||
|
||||
```js
|
||||
{
|
||||
kind: 1111,
|
||||
content: 'Great blog post!',
|
||||
tags: [
|
||||
// top-level comments scope to event addresses or ids
|
||||
["A", "30023:3c9849383bdea883b0bd16fece1ed36d37e37cdde3ce43b17ea4e9192ec11289:f9347ca7", "wss://example.relay"],
|
||||
// the root kind
|
||||
["K", "30023"],
|
||||
|
||||
// the parent event address (same as root for top-level comments)
|
||||
["a", "30023:3c9849383bdea883b0bd16fece1ed36d37e37cdde3ce43b17ea4e9192ec11289:f9347ca7", "wss://example.relay"],
|
||||
// when the parent event is replaceable or addressable, also include an `e` tag referencing its id
|
||||
["e", "5b4fc7fed15672fefe65d2426f67197b71ccc82aa0cc8a9e94f683eb78e07651", "wss://example.relay"],
|
||||
// the parent event kind
|
||||
["k", "30023"]
|
||||
]
|
||||
// other fields
|
||||
}
|
||||
```
|
||||
|
||||
A comment on a [NIP-94](94.md) file looks like this:
|
||||
|
||||
```js
|
||||
{
|
||||
kind: 1111,
|
||||
content: 'Great file!',
|
||||
tags: [
|
||||
// top-level comments have the same scope and reply to addresses or ids
|
||||
["E", "768ac8720cdeb59227cf95e98b66560ef03d8bc9a90d721779e76e68fb42f5e6", "wss://example.relay", "3721e07b079525289877c366ccab47112bdff3d1b44758ca333feb2dbbbbe5bb"],
|
||||
// the root kind
|
||||
["K", "1063"],
|
||||
|
||||
// the parent event id (same as root for top-level comments)
|
||||
["e", "768ac8720cdeb59227cf95e98b66560ef03d8bc9a90d721779e76e68fb42f5e6", "wss://example.relay", "3721e07b079525289877c366ccab47112bdff3d1b44758ca333feb2dbbbbe5bb"],
|
||||
// the parent kind
|
||||
["k", "1063"]
|
||||
]
|
||||
// other fields
|
||||
}
|
||||
```
|
||||
|
||||
A reply to a comment looks like this:
|
||||
|
||||
```js
|
||||
{
|
||||
kind: 1111,
|
||||
content: 'This is a reply to "Great file!"',
|
||||
tags: [
|
||||
// nip-94 file event id
|
||||
["E", "768ac8720cdeb59227cf95e98b66560ef03d8bc9a90d721779e76e68fb42f5e6", "wss://example.relay", "fd913cd6fa9edb8405750cd02a8bbe16e158b8676c0e69fdc27436cc4a54cc9a"],
|
||||
// the root kind
|
||||
["K", "1063"],
|
||||
|
||||
// the parent event
|
||||
["e", "5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36", "wss://example.relay", "93ef2ebaaf9554661f33e79949007900bbc535d239a4c801c33a4d67d3e7f546"],
|
||||
// the parent kind
|
||||
["k", "1111"]
|
||||
]
|
||||
// other fields
|
||||
}
|
||||
```
|
||||
|
||||
A comment on a website's url looks like this:
|
||||
|
||||
```js
|
||||
{
|
||||
kind: 1111,
|
||||
content: 'Nice article!',
|
||||
tags: [
|
||||
// referencing the root url
|
||||
["I", "https://abc.com/articles/1"],
|
||||
// the root "kind": for an url, the kind is its domain
|
||||
["K", "https://abc.com"],
|
||||
|
||||
// the parent reference (same as root for top-level comments)
|
||||
["i", "https://abc.com/articles/1"],
|
||||
// the parent "kind": for an url, the kind is its domain
|
||||
["k", "https://abc.com"]
|
||||
]
|
||||
// other fields
|
||||
}
|
||||
```
|
||||
|
||||
A podcast comment example:
|
||||
|
||||
```js
|
||||
{
|
||||
id: "80c48d992a38f9c445b943a9c9f1010b396676013443765750431a9004bdac05",
|
||||
pubkey: "252f10c83610ebca1a059c0bae8255eba2f95be4d1d7bcfa89d7248a82d9f111",
|
||||
kind: 1111,
|
||||
content: "This was a great episode!",
|
||||
tags: [
|
||||
// podcast episode reference
|
||||
["I", "podcast:item:guid:d98d189b-dc7b-45b1-8720-d4b98690f31f", "https://fountain.fm/episode/z1y9TMQRuqXl2awyrQxg"],
|
||||
// podcast episode type
|
||||
["K", "podcast:item:guid"],
|
||||
|
||||
// same value as "I" tag above, because it is a top-level comment (not a reply to a comment)
|
||||
["i", "podcast:item:guid:d98d189b-dc7b-45b1-8720-d4b98690f31f", "https://fountain.fm/episode/z1y9TMQRuqXl2awyrQxg"],
|
||||
["k", "podcast:item:guid"]
|
||||
]
|
||||
// other fields
|
||||
}
|
||||
```
|
||||
|
||||
A reply to a podcast comment:
|
||||
|
||||
```js
|
||||
{
|
||||
kind: 1111,
|
||||
content: "I'm replying to the above comment.",
|
||||
tags: [
|
||||
// podcast episode reference
|
||||
["I", "podcast:item:guid:d98d189b-dc7b-45b1-8720-d4b98690f31f", "https://fountain.fm/episode/z1y9TMQRuqXl2awyrQxg"],
|
||||
// podcast episode type
|
||||
["K", "podcast:item:guid"],
|
||||
|
||||
// this is a reference to the above comment
|
||||
["e", "80c48d992a38f9c445b943a9c9f1010b396676013443765750431a9004bdac05", "wss://example.relay", "252f10c83610ebca1a059c0bae8255eba2f95be4d1d7bcfa89d7248a82d9f111"],
|
||||
// the parent comment kind
|
||||
["k", "1111"]
|
||||
]
|
||||
// other fields
|
||||
}
|
||||
```
|
||||
46
29.md
46
29.md
@@ -66,28 +66,7 @@ These are the events expected to be found in NIP-29 groups.
|
||||
|
||||
These events generally can be sent by all members of a group and they require the `h` tag to be present so they're attached to a specific group.
|
||||
|
||||
- *text root note* (`kind:11`)
|
||||
|
||||
This is the basic unit of a "microblog" root text note sent to a group.
|
||||
|
||||
```jsonc
|
||||
"kind": 11,
|
||||
"content": "hello my friends lovers of pizza",
|
||||
"tags": [
|
||||
["h", "<group-id>"],
|
||||
["previous", "<event-id-first-chars>", "<event-id-first-chars>", /*...*/]
|
||||
]
|
||||
// other fields...
|
||||
```
|
||||
|
||||
- *threaded text reply* (`kind:12`)
|
||||
|
||||
This is the basic unit of a "microblog" reply note sent to a group. It's the same as `kind:11`, except for the fact that it must be used whenever it's in reply to some other note (either in reply to a `kind:11` or a `kind:12`). `kind:12` events SHOULD use NIP-10 markers, leaving an empty relay url:
|
||||
|
||||
* `["e", "<kind-11-root-id>", "", "root"]`
|
||||
* `["e", "<kind-12-event-id>", "", "reply"]`
|
||||
|
||||
- *chat message* (`kind:9`)
|
||||
- _chat message_ (`kind:9`)
|
||||
|
||||
This is the basic unit of a _chat message_ sent to a group.
|
||||
|
||||
@@ -101,15 +80,23 @@ This is the basic unit of a _chat message_ sent to a group.
|
||||
// other fields...
|
||||
```
|
||||
|
||||
- *chat message threaded reply* (`kind:10`)
|
||||
- _thread root post_ (`kind:11`)
|
||||
|
||||
Similar to `kind:12`, this is the basic unit of a chat message sent to a group. This is intended for in-chat threads that may be hidden by default. Not all in-chat replies MUST use `kind:10`, only when the intention is to create a hidden thread that isn't part of the normal flow of the chat (although clients are free to display those by default too).
|
||||
This is the basic unit of a forum-like root thread post sent to a group.
|
||||
|
||||
`kind:10` SHOULD use NIP-10 markers, just like `kind:12`.
|
||||
```jsonc
|
||||
"kind": 11,
|
||||
"content": "hello my friends lovers of pizza",
|
||||
"tags": [
|
||||
["h", "<group-id>"],
|
||||
["previous", "<event-id-first-chars>", "<event-id-first-chars>", /*...*/]
|
||||
]
|
||||
// other fields...
|
||||
```
|
||||
|
||||
- other events:
|
||||
- _other events_:
|
||||
|
||||
Groups may also accept other events, like long-form articles, calendar, livestream, market announcements and so on. These should be as defined in their respective NIPs, with the addition of the `h` tag.
|
||||
Groups may also accept other events, like [NIP-22](22.md) comments as threaded replies to both chats messages and threads, long-form articles, calendar, livestreams, market announcements and so on. These should be as defined in their respective NIPs, with the addition of the `h` tag.
|
||||
|
||||
### User-related group management events
|
||||
|
||||
@@ -169,12 +156,13 @@ Each moderation action uses a different kind and requires different arguments, w
|
||||
|
||||
| kind | name | tags |
|
||||
| --- | --- | --- |
|
||||
| 9000 | `add-user` | `p` with pubkey hex and optional roles |
|
||||
| 9000 | `put-user` | `p` with pubkey hex and optional roles |
|
||||
| 9001 | `remove-user` | `p` with pubkey hex |
|
||||
| 9002 | `edit-metadata` | fields from `kind:39000` to be modified |
|
||||
| 9005 | `delete-event` | |
|
||||
| 9005 | `delete-event` | `e` with event id hex |
|
||||
| 9007 | `create-group` | |
|
||||
| 9008 | `delete-group` | |
|
||||
| 9009 | `create-invite` | |
|
||||
|
||||
It's expected that the group state (of who is an allowed member or not, who is an admin and with which permission or not, what are the group name and picture etc) can be fully reconstructed from the canonical sequence of these events.
|
||||
|
||||
|
||||
197
46.md
197
46.md
@@ -6,7 +6,7 @@ Nostr Remote Signing
|
||||
|
||||
## Changes
|
||||
|
||||
`remote-signer-key` is introduced, passed in bunker url, clients must differentiate between `remote-signer-pubkey` and `user-pubkey`, must call `get_public_key` after connect.
|
||||
`remote-signer-key` is introduced, passed in bunker url, clients must differentiate between `remote-signer-pubkey` and `user-pubkey`, must call `get_public_key` after connect, nip05 login is removed, create_account moved to another NIP.
|
||||
|
||||
## Rationale
|
||||
|
||||
@@ -25,6 +25,14 @@ This NIP describes a method for 2-way communication between a remote signer and
|
||||
|
||||
All pubkeys specified in this NIP are in hex format.
|
||||
|
||||
## Overview
|
||||
|
||||
1. _client_ generates `client-keypair`. This keypair doesn't need to be communicated to _user_ since it's largely disposable. _client_ might choose to store it locally and they should delete it on logout;
|
||||
2. A connection is established (see below), _remote-signer_ learns `client-pubkey`, _client_ learns `remote-signer-pubkey`.
|
||||
3. _client_ uses `client-keypair` to send requests to _remote-signer_ by `p`-tagging and encrypting to `remote-signer-pubkey`;
|
||||
4. _remote-signer_ responds to _client_ by `p`-tagging and encrypting to the `client-pubkey`.
|
||||
5. _client_ requests `get_public_key` to learn `user-pubkey`.
|
||||
|
||||
## Initiating a connection
|
||||
|
||||
There are two ways to initiate a connection:
|
||||
@@ -37,66 +45,16 @@ _remote-signer_ provides connection token in the form:
|
||||
bunker://<remote-signer-pubkey>?relay=<wss://relay-to-connect-on>&relay=<wss://another-relay-to-connect-on>&secret=<optional-secret-value>
|
||||
```
|
||||
|
||||
_user_ pastes this token on _client_, which then uses the details to connect to _remote-signer_ via the specified relays. Optional secret can be used for single successfully established connection only, _remote-signer_ SHOULD ignore new attempts to establish connection with old optional secret.
|
||||
_user_ passes this token to _client_, which then sends `connect` request to _remote-signer_ via the specified relays. Optional secret can be used for single successfully established connection only, _remote-signer_ SHOULD ignore new attempts to establish connection with old secret.
|
||||
|
||||
### Direct connection initiated by the client
|
||||
### Direct connection initiated by the _client_
|
||||
|
||||
In this case, basically the opposite direction of the first case, _client_ provides a connection token (or encodes the token in a QR code) and _remote-signer_ initiates a connection via the specified relays.
|
||||
_client_ provides a connection token in the form:
|
||||
|
||||
```
|
||||
nostrconnect://<client-pubkey>?relay=<wss://relay-to-connect-on>&metadata=<json metadata in the form: {"name":"...", "url": "...", "description": "..."}>
|
||||
nostrconnect://<client-pubkey>?relay=<wss://relay-to-connect-on>&metadata=<json metadata: {"name":"...", "url": "...", "description": "...", "perms": "..."}>&secret=<required-secret-value>
|
||||
```
|
||||
|
||||
## The flow
|
||||
|
||||
1. _client_ generates `client-keypair`. This keypair doesn't need to be communicated to _user_ since it's largely disposable. _client_ might choose to store it locally and they should delete it on logout;
|
||||
2. _client_ gets `remote-signer-pubkey` (either via a `bunker://` connection string or a NIP-05 login-flow; shown below);
|
||||
3. _client_ use `client-keypair` to send requests to _remote-signer_ by `p`-tagging and encrypting to `remote-signer-pubkey`;
|
||||
4. _remote-signer_ responds to _client_ by `p`-tagging and encrypting to the `client-pubkey`.
|
||||
|
||||
### Example flow for signing an event
|
||||
|
||||
- `remote-signer-pubkey` is `fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52`
|
||||
- `user-pubkey` is also `fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52`
|
||||
- `client-pubkey` is `eff37350d839ce3707332348af4549a96051bd695d3223af4aabce4993531d86`
|
||||
|
||||
#### Signature request
|
||||
|
||||
```js
|
||||
{
|
||||
"kind": 24133,
|
||||
"pubkey": "eff37350d839ce3707332348af4549a96051bd695d3223af4aabce4993531d86",
|
||||
"content": nip04({
|
||||
"id": <random_string>,
|
||||
"method": "sign_event",
|
||||
"params": [json_stringified(<{
|
||||
content: "Hello, I'm signing remotely",
|
||||
kind: 1,
|
||||
tags: [],
|
||||
created_at: 1714078911
|
||||
}>)]
|
||||
}),
|
||||
"tags": [["p", "fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52"]], // p-tags the remote-signer-pubkey
|
||||
}
|
||||
```
|
||||
|
||||
#### Response event
|
||||
|
||||
```js
|
||||
{
|
||||
"kind": 24133,
|
||||
"pubkey": "fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52",
|
||||
"content": nip04({
|
||||
"id": <random_string>,
|
||||
"result": json_stringified(<signed-event>)
|
||||
}),
|
||||
"tags": [["p", "eff37350d839ce3707332348af4549a96051bd695d3223af4aabce4993531d86"]], // p-tags the client-pubkey
|
||||
}
|
||||
```
|
||||
|
||||
#### Diagram
|
||||
|
||||

|
||||
_user_ passes this token to _remote-signer_, which then sends `connect` *response* event to the `client-pubkey` via the specified relays. Client discovers `remote-signer-pubkey` from connect response author. `secret` value MUST be provided to avoid connection spoofing, _client_ MUST validate the `secret` returned by `connect` response.
|
||||
|
||||
## Request Events `kind: 24133`
|
||||
|
||||
@@ -125,11 +83,11 @@ The `content` field is a JSON-RPC-like message that is [NIP-04](04.md) encrypted
|
||||
|
||||
### Methods/Commands
|
||||
|
||||
Each of the following are methods that the client sends to the remote signer.
|
||||
Each of the following are methods that the _client_ sends to the _remote-signer_.
|
||||
|
||||
| Command | Params | Result |
|
||||
| ------------------------ | ------------------------------------------------- | ---------------------------------------------------------------------- |
|
||||
| `connect` | `[<user_pubkey>, <optional_secret>, <optional_requested_permissions>]` | "ack" |
|
||||
| `connect` | `[<remote-signer-pubkey>, <optional_secret>, <optional_requested_permissions>]` | "ack" OR `<required-secret-value>` |
|
||||
| `sign_event` | `[<{kind, content, tags, created_at}>]` | `json_stringified(<signed_event>)` |
|
||||
| `ping` | `[]` | "pong" |
|
||||
| `get_relays` | `[]` | `json_stringified({<relay_url>: {read: <boolean>, write: <boolean>}})` |
|
||||
@@ -138,11 +96,10 @@ Each of the following are methods that the client sends to the remote signer.
|
||||
| `nip04_decrypt` | `[<third_party_pubkey>, <nip04_ciphertext_to_decrypt>]` | `<plaintext>` |
|
||||
| `nip44_encrypt` | `[<third_party_pubkey>, <plaintext_to_encrypt>]` | `<nip44_ciphertext>` |
|
||||
| `nip44_decrypt` | `[<third_party_pubkey>, <nip44_ciphertext_to_decrypt>]` | `<plaintext>` |
|
||||
| `create_account` | `[<username>, <domain>, <optional_email>, <optional_requested_permissions>]` | `<newly_created_user_pubkey>` |
|
||||
|
||||
### Requested permissions
|
||||
|
||||
The `connect` method may be provided with `optional_requested_permissions` for user convenience. The permissions are a comma-separated list of `method[:params]`, i.e. `nip04_encrypt,sign_event:4` meaning permissions to call `nip04_encrypt` and to call `sign_event` with `kind:4`. Optional parameter for `sign_event` is the kind number, parameters for other methods are to be defined later.
|
||||
The `connect` method may be provided with `optional_requested_permissions` for user convenience. The permissions are a comma-separated list of `method[:params]`, i.e. `nip04_encrypt,sign_event:4` meaning permissions to call `nip04_encrypt` and to call `sign_event` with `kind:4`. Optional parameter for `sign_event` is the kind number, parameters for other methods are to be defined later. Same permission format may be used for `perms` field of `metadata` in `nostrconnect://` string.
|
||||
|
||||
## Response Events `kind:24133`
|
||||
|
||||
@@ -171,9 +128,54 @@ The `content` field is a JSON-RPC-like message that is [NIP-04](04.md) encrypted
|
||||
- `results` is a string of the result of the call (this can be either a string or a JSON stringified object)
|
||||
- `error`, _optionally_, it is an error in string form, if any. Its presence indicates an error with the request.
|
||||
|
||||
### Auth Challenges
|
||||
## Example flow for signing an event
|
||||
|
||||
An Auth Challenge is a response that a remote signer can send back when it needs the user to authenticate via other means. This is currently used in the OAuth-like flow enabled by signers like [Nsecbunker](https://github.com/kind-0/nsecbunkerd/). The response `content` object will take the following form:
|
||||
- `remote-signer-pubkey` is `fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52`
|
||||
- `user-pubkey` is also `fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52`
|
||||
- `client-pubkey` is `eff37350d839ce3707332348af4549a96051bd695d3223af4aabce4993531d86`
|
||||
|
||||
### Signature request
|
||||
|
||||
```js
|
||||
{
|
||||
"kind": 24133,
|
||||
"pubkey": "eff37350d839ce3707332348af4549a96051bd695d3223af4aabce4993531d86",
|
||||
"content": nip04({
|
||||
"id": <random_string>,
|
||||
"method": "sign_event",
|
||||
"params": [json_stringified(<{
|
||||
content: "Hello, I'm signing remotely",
|
||||
kind: 1,
|
||||
tags: [],
|
||||
created_at: 1714078911
|
||||
}>)]
|
||||
}),
|
||||
"tags": [["p", "fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52"]], // p-tags the remote-signer-pubkey
|
||||
}
|
||||
```
|
||||
|
||||
### Response event
|
||||
|
||||
```js
|
||||
{
|
||||
"kind": 24133,
|
||||
"pubkey": "fa984bd7dbb282f07e16e7ae87b26a2a7b9b90b7246a44771f0cf5ae58018f52",
|
||||
"content": nip04({
|
||||
"id": <random_string>,
|
||||
"result": json_stringified(<signed-event>)
|
||||
}),
|
||||
"tags": [["p", "eff37350d839ce3707332348af4549a96051bd695d3223af4aabce4993531d86"]], // p-tags the client-pubkey
|
||||
}
|
||||
```
|
||||
|
||||
### Diagram
|
||||
|
||||

|
||||
|
||||
|
||||
## Auth Challenges
|
||||
|
||||
An Auth Challenge is a response that a _remote-signer_ can send back when it needs the _user_ to authenticate via other means. The response `content` object will take the following form:
|
||||
|
||||
```json
|
||||
{
|
||||
@@ -183,42 +185,57 @@ An Auth Challenge is a response that a remote signer can send back when it needs
|
||||
}
|
||||
```
|
||||
|
||||
Clients should display (in a popup or new tab) the URL from the `error` field and then subscribe/listen for another response from the remote signer (reusing the same request ID). This event will be sent once the user authenticates in the other window (or will never arrive if the user doesn't authenticate). It's also possible to add a `redirect_uri` url parameter to the auth_url, which is helpful in situations when a client cannot open a new window or tab to display the auth challenge.
|
||||
_client_ should display (in a popup or new tab) the URL from the `error` field and then subscribe/listen for another response from the _remote-signer_ (reusing the same request ID). This event will be sent once the user authenticates in the other window (or will never arrive if the user doesn't authenticate).
|
||||
|
||||
#### Example event signing request with auth challenge
|
||||
### Example event signing request with auth challenge
|
||||
|
||||
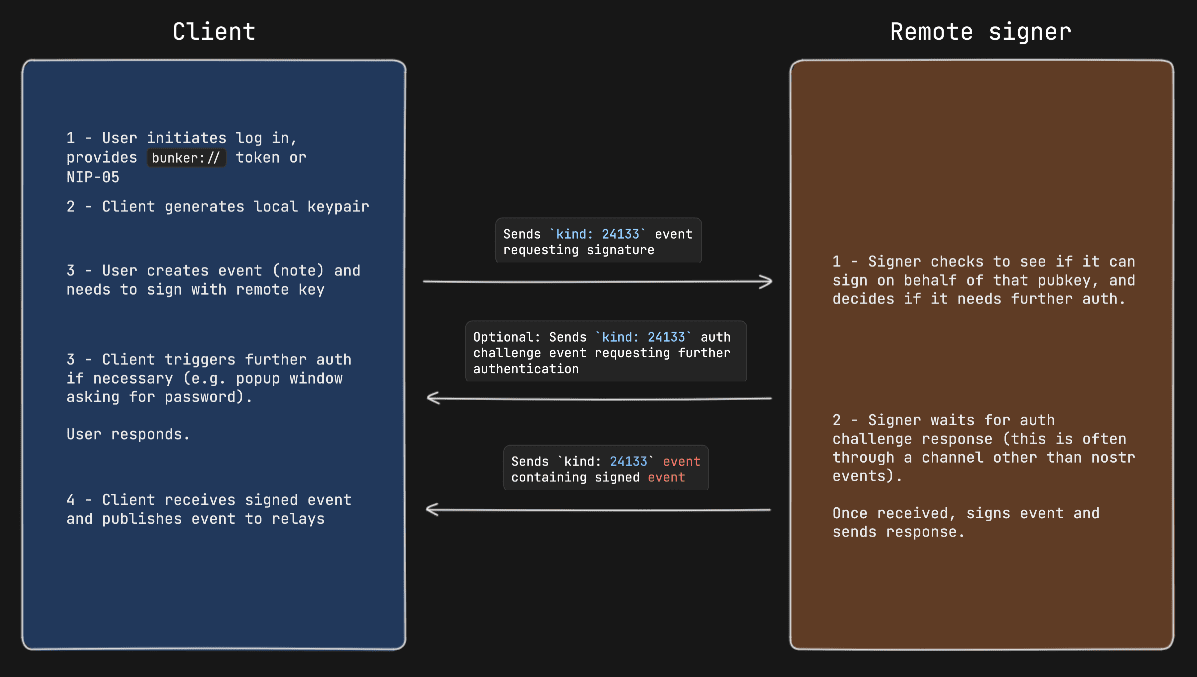
|
||||
|
||||
## Pure public key login
|
||||
|
||||
A _client_ SHOULD support logins with just an `npub`, an `nprofile` or a NIP-05 address instead of requiring a full `bunker://...` URI. In order to do that, it can follow these steps:
|
||||
|
||||
1. Read _user-pubkey_ from the provided NIP-05, `nprofile` or `npub` code;
|
||||
2. Acquire the list of outbox relays for _user_ (either by fetching the user's `kind:10002` relay list from relay hints or hardcoded relays or by other means);
|
||||
3. Query these relay for a `kind:10046` event from _user_;
|
||||
4. Read NIP-46 bunker connection metadata from that event -- then proceed as if the user had typed that bunker URI.
|
||||
|
||||
For this to work _user_ must have somehow published such `kind:10046` event beforehand (which might be a job for the bunker provider or app directly or not).
|
||||
|
||||
### `kind:10046` event format:
|
||||
|
||||
```jsonc
|
||||
{
|
||||
"pubkey": "<user-pubkey>",
|
||||
"kind": 10046,
|
||||
"tags": [
|
||||
["relays", "<remote-signer-relay-url>", "<any-number-of-other-relay-urls...>"],
|
||||
["pubkey", "<remote-signer-pubkey>"]
|
||||
]
|
||||
}
|
||||
```
|
||||
|
||||
## Appendix
|
||||
|
||||
### NIP-05 Login Flow
|
||||
### Announcing _remote-signer_ metadata
|
||||
|
||||
Clients might choose to present a more familiar login flow, so users can type a NIP-05 address instead of a `bunker://` string.
|
||||
_remote-signer_ MAY publish it's metadata by using [NIP-05](05.md) and [NIP-89](89.md). With NIP-05, a request to `<remote-signer>/.well-known/nostr.json?name=_` MAY return this:
|
||||
```
|
||||
{
|
||||
"names":{
|
||||
"_": <remote-signer-app-pubkey>,
|
||||
},
|
||||
"nip46": {
|
||||
"relays": ["wss://relay1","wss://relay2"...],
|
||||
"nostrconnect_url": "https://remote-signer-domain.com/<nostrconnect>"
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
When the user types a NIP-05 the client:
|
||||
The `<remote-signer-app-pubkey>` MAY be used to verify the domain from _remote-signer_'s NIP-89 event (see below). `relays` SHOULD be used to construct a more precise `nostrconnect://` string for the specific `remote-signer`. `nostrconnect_url` template MAY be used to redirect users to _remote-signer_'s connection flow by replacing `<nostrconnect>` placeholder with an actual `nostrconnect://` string.
|
||||
|
||||
- Queries the `/.well-known/nostr.json` file from the domain for the NIP-05 address provided to get the user's pubkey (this is the `user-pubkey`)
|
||||
- In the same `/.well-known/nostr.json` file, queries for the `nip46` key to get the relays that the remote signer will be listening on.
|
||||
- Now the client has enough information to send commands to the remote signer on behalf of the user.
|
||||
### Remote signer discovery via NIP-89
|
||||
|
||||
### OAuth-like Flow
|
||||
_remote-signer_ MAY publish a NIP-89 `kind: 31990` event with `k` tag of `24133`, which MAY also include one or more `relay` tags and MAY include `nostrconnect_url` tag. The semantics of `relay` and `nostrconnect_url` tags are the same as in the section above.
|
||||
|
||||
#### Remote signer discovery via NIP-89
|
||||
|
||||
In this last case, most often used to facilitate an OAuth-like signin flow, the client first looks for remote signers that have announced themselves via NIP-89 application handler events.
|
||||
|
||||
First the client will query for `kind: 31990` events that have a `k` tag of `24133`.
|
||||
|
||||
These are generally shown to a user, and once the user selects which remote signer to use and provides the `user-pubkey` they want to use (via npub, pubkey, or nip-05 value), the client can initiate a connection. Note that it's on the user to select the _remote-signer_ that is actually managing the `user-keypair` that they would like to use in this case. If the `user-pubkey` is managed on another _remote-signer_ the connection will fail.
|
||||
|
||||
In addition, it's important that clients validate that the pubkey of the announced _remote-signer_ matches the pubkey of the `_` entry in the `/.well-known/nostr.json` file of the remote signer's announced domain.
|
||||
|
||||
Clients that allow users to create new accounts should also consider validating the availability of a given username in the namespace of remote signer's domain by checking the `/.well-known/nostr.json` file for existing usernames. Clients can then show users feedback in the UI before sending a `create_account` event to the remote signer and receiving an error in return. Ideally, remote signers would also respond with understandable error messages if a client tries to create an account with an existing username.
|
||||
|
||||
#### Example Oauth-like flow to create a new user account with Nsecbunker
|
||||
|
||||
Coming soon...
|
||||
|
||||
## References
|
||||
|
||||
- [NIP-04 - Encryption](04.md)
|
||||
_client_ MAY improve UX by discovering _remote-signers_ using their `kind: 31990` events. _client_ MAY then pre-generate `nostrconnect://` strings for the _remote-signers_, and SHOULD in that case verify that `kind: 31990` event's author is mentioned in signer's `nostr.json?name=_` file as `<remote-signer-app-pubkey>`.
|
||||
|
||||
2
53.md
2
53.md
@@ -119,4 +119,4 @@ Common use cases include meeting rooms/workshops, watch-together activities, or
|
||||
"content": "Zaps to live streams is beautiful.",
|
||||
"sig": "997f62ddfc0827c121043074d50cfce7a528e978c575722748629a4137c45b75bdbc84170bedc723ef0a5a4c3daebf1fef2e93f5e2ddb98e5d685d022c30b622"
|
||||
}
|
||||
````
|
||||
```
|
||||
|
||||
2
57.md
2
57.md
@@ -66,7 +66,7 @@ A signed `zap request` event is not published, but is instead sent using a HTTP
|
||||
- `nostr` is the `9734` `zap request` event, JSON encoded then URI encoded
|
||||
- `lnurl` is the lnurl pay url of the recipient, encoded using bech32 with the prefix `lnurl`
|
||||
|
||||
This request should return a JSON response with a `pr` key, which is the invoice the sender must pay to finalize his zap. Here is an example flow in javascript:
|
||||
This request should return a JSON response with a `pr` key, which is the invoice the sender must pay to finalize their zap. Here is an example flow in javascript:
|
||||
|
||||
```javascript
|
||||
const senderPubkey // The sender's pubkey
|
||||
|
||||
2
59.md
2
59.md
@@ -245,7 +245,7 @@ const rumor = createRumor(
|
||||
const seal = createSeal(rumor, senderPrivateKey, recipientPublicKey)
|
||||
const wrap = createWrap(seal, recipientPublicKey)
|
||||
|
||||
// Recipient unwraps with his/her private key.
|
||||
// Recipient unwraps with their private key.
|
||||
|
||||
const unwrappedSeal = nip44Decrypt(wrap, recipientPrivateKey)
|
||||
const unsealedRumor = nip44Decrypt(unwrappedSeal, recipientPrivateKey)
|
||||
|
||||
86
69.md
Normal file
86
69.md
Normal file
@@ -0,0 +1,86 @@
|
||||
# NIP-69
|
||||
|
||||
## Peer-to-peer Order events
|
||||
|
||||
`draft` `optional`
|
||||
|
||||
## Abstract
|
||||
|
||||
Peer-to-peer (P2P) platforms have seen an upturn in recent years, while having more and more options is positive, in the specific case of p2p, having several options contributes to the liquidity split, meaning sometimes there's not enough assets available for trading. If we combine all these individual solutions into one big pool of orders, it will make them much more competitive compared to centralized systems, where a single authority controls the liquidity.
|
||||
|
||||
This NIP defines a simple standard for peer-to-peer order events, which enables the creation of a big liquidity pool for all p2p platforms participating.
|
||||
|
||||
## The event
|
||||
|
||||
Events are [addressable events](https://github.com/nostr-protocol/nips/blob/master/01.md#kinds) and use `38383` as event kind, a p2p event look like this:
|
||||
|
||||
```json
|
||||
{
|
||||
"id": "84fad0d29cb3529d789faeff2033e88fe157a48e071c6a5d1619928289420e31",
|
||||
"pubkey": "dbe0b1be7aafd3cfba92d7463edbd4e33b2969f61bd554d37ac56f032e13355a",
|
||||
"created_at": 1702548701,
|
||||
"kind": 38383,
|
||||
"tags": [
|
||||
["d", "ede61c96-4c13-4519-bf3a-dcf7f1e9d842"],
|
||||
["k", "sell"],
|
||||
["f", "VES"],
|
||||
["s", "pending"],
|
||||
["amt", "0"],
|
||||
["fa", "100"],
|
||||
["pm", "face to face", "bank transfer"],
|
||||
["premium", "1"],
|
||||
[
|
||||
"rating",
|
||||
"{\"total_reviews\":1,\"total_rating\":3.0,\"last_rating\":3,\"max_rate\":5,\"min_rate\":1}"
|
||||
],
|
||||
["source", "https://t.me/p2plightning/xxxxxxx"],
|
||||
["network", "mainnet"],
|
||||
["layer", "lightning"],
|
||||
["name", "Nakamoto"],
|
||||
["g", "<geohash>"],
|
||||
["bond", "0"],
|
||||
["expiration", "1719391096"],
|
||||
["y", "lnp2pbot"],
|
||||
["z", "order"]
|
||||
],
|
||||
"content": "",
|
||||
"sig": "7e8fe1eb644f33ff51d8805c02a0e1a6d034e6234eac50ef7a7e0dac68a0414f7910366204fa8217086f90eddaa37ded71e61f736d1838e37c0b73f6a16c4af2"
|
||||
}
|
||||
```
|
||||
|
||||
## Tags
|
||||
|
||||
- `d` < Order ID >: A unique identifier for the order.
|
||||
- `k` < Order type >: `sell` or `buy`.
|
||||
- `f` < Currency >: The asset being traded, using the [ISO 4217](https://en.wikipedia.org/wiki/ISO_4217) standard.
|
||||
- `s` < Status >: `pending`, `canceled`, `in-progress`, `success`.
|
||||
- `amt` < Amount >: The amount of Bitcoin to be traded, the amount is defined in satoshis, if `0` means that the amount of satoshis will be obtained from a public API after the taker accepts the order.
|
||||
- `fa` < Fiat amount >: The fiat amount being traded, for range orders two values are expected, the minimum and maximum amount.
|
||||
- `pm` < Payment method >: The payment method used for the trade, if the order has multiple payment methods, they should be separated by a comma.
|
||||
- `premium` < Premium >: The percentage of the premium the maker is willing to pay.
|
||||
- `source` [Source]: The source of the order, it can be a URL that redirects to the order.
|
||||
- `rating` [Rating]: The rating of the maker, this document does not define how the rating is calculated, it's up to the platform to define it.
|
||||
- `network` < Network >: The network used for the trade, it can be `mainnet`, `testnet`, `signet`, etc.
|
||||
- `layer` < Layer >: The layer used for the trade, it can be `onchain`, `lightning`, `liquid`, etc.
|
||||
- `name` [Name]: The name of the maker.
|
||||
- `g` [Geohash]: The geohash of the operation, it can be useful in a face to face trade.
|
||||
- `bond` [Bond]: The bond amount, the bond is a security deposit that both parties must pay.
|
||||
- `expiration` < Expiration\>: The expiration date of the order ([NIP-40](https://github.com/nostr-protocol/nips/blob/master/40.md)).
|
||||
- `y` < Platform >: The platform that created the order.
|
||||
- `z` < Document >: `order`.
|
||||
|
||||
Mandatory tags are enclosed with `<tag>`, optional tags are enclosed with `[tag]`.
|
||||
|
||||
## Implementations
|
||||
|
||||
Currently implemented on the following platforms:
|
||||
|
||||
- [Mostro](https://github.com/MostroP2P/mostro)
|
||||
- [@lnp2pBot](https://github.com/lnp2pBot/bot)
|
||||
- [Robosats](https://github.com/RoboSats/robosats/pull/1362)
|
||||
|
||||
## References
|
||||
|
||||
- [Mostro protocol specification](https://mostro.network/protocol/)
|
||||
- [Messages specification for peer 2 peer NIP proposal](https://github.com/nostr-protocol/nips/blob/8250274a22f4882f621510df0054fd6167c10c9e/31001.md)
|
||||
- [n3xB](https://github.com/nobu-maeda/n3xb)
|
||||
25
README.md
25
README.md
@@ -40,6 +40,7 @@ They exist to document what may be implemented by [Nostr](https://github.com/nos
|
||||
- [NIP-18: Reposts](18.md)
|
||||
- [NIP-19: bech32-encoded entities](19.md)
|
||||
- [NIP-21: `nostr:` URI scheme](21.md)
|
||||
- [NIP-22: Comment](22.md)
|
||||
- [NIP-23: Long-form Content](23.md)
|
||||
- [NIP-24: Extra metadata fields and tags](24.md)
|
||||
- [NIP-25: Reactions](25.md)
|
||||
@@ -77,6 +78,7 @@ They exist to document what may be implemented by [Nostr](https://github.com/nos
|
||||
- [NIP-61: Nutzaps](61.md)
|
||||
- [NIP-64: Chess (PGN)](64.md)
|
||||
- [NIP-65: Relay List Metadata](65.md)
|
||||
- [NIP-69: Peer-to-peer Order events](69.md)
|
||||
- [NIP-70: Protected Events](70.md)
|
||||
- [NIP-71: Video Events](71.md)
|
||||
- [NIP-72: Moderated Communities](72.md)
|
||||
@@ -217,6 +219,7 @@ They exist to document what may be implemented by [Nostr](https://github.com/nos
|
||||
| `34236` | Short-form Portrait Video Event | [71](71.md) |
|
||||
| `34550` | Community Definition | [72](72.md) |
|
||||
| `37375` | Cashu Wallet Event | [60](60.md) |
|
||||
| `38383` | Peer-to-peer Order events | [69](69.md) |
|
||||
| `39000-9` | Group metadata events | [29](29.md) |
|
||||
|
||||
[NUD: Custom Feeds]: https://wikifreedia.xyz/cip-01/
|
||||
@@ -258,22 +261,32 @@ They exist to document what may be implemented by [Nostr](https://github.com/nos
|
||||
|
||||
| name | value | other parameters | NIP |
|
||||
| ----------------- | ------------------------------------ | ------------------------------- | -------------------------------------------------- |
|
||||
| `e` | event id (hex) | relay URL, marker, pubkey (hex) | [01](01.md), [10](10.md) |
|
||||
| `p` | pubkey (hex) | relay URL, petname | [01](01.md), [02](02.md) |
|
||||
| `a` | coordinates to an event | relay URL | [01](01.md) |
|
||||
| `A` | root address | relay URL | [22](22.md) |
|
||||
| `d` | identifier | -- | [01](01.md) |
|
||||
| `-` | -- | -- | [70](70.md) |
|
||||
| `e` | event id (hex) | relay URL, marker, pubkey (hex) | [01](01.md), [10](10.md) |
|
||||
| `E` | root event i | relay URL | [22](22.md) |
|
||||
| `f` | currency code | -- | [69](69.md) |
|
||||
| `g` | geohash | -- | [52](52.md) |
|
||||
| `h` | group id | -- | [29](29.md) |
|
||||
| `i` | external identity | proof, url hint | [39](39.md), [73](73.md) |
|
||||
| `i` | external identity | proof, url hint | [35](35.md), [39](39.md), [73](73.md) |
|
||||
| `I` | root external identity | -- | [22](22.md) |
|
||||
| `k` | kind | -- | [18](18.md), [25](25.md), [72](72.md), [73](73.md) |
|
||||
| `K` | root scope | -- | [22](22.md) |
|
||||
| `l` | label, label namespace | -- | [32](32.md) |
|
||||
| `L` | label namespace | -- | [32](32.md) |
|
||||
| `m` | MIME type | -- | [94](94.md) |
|
||||
| `p` | pubkey (hex) | relay URL, petname | [01](01.md), [02](02.md) |
|
||||
| `q` | event id (hex) | relay URL, pubkey (hex) | [18](18.md) |
|
||||
| `r` | a reference (URL, etc) | -- | [24](24.md), [25](25.md) |
|
||||
| `r` | relay url | marker | [65](65.md) |
|
||||
| `t` | hashtag | -- | [24](24.md), [34](34.md) |
|
||||
| `s` | status | -- | [69](69.md) |
|
||||
| `t` | hashtag | -- | [24](24.md), [34](34.md), [35](35.md) |
|
||||
| `u` | url | -- | [61](61.md), [98](98.md) |
|
||||
| `x` | infohash | -- | [35](35.md) |
|
||||
| `y` | platform | -- | [69](69.md) |
|
||||
| `z` | order number | -- | [69](69.md) |
|
||||
| `-` | -- | -- | [70](70.md) |
|
||||
| `alt` | summary | -- | [31](31.md) |
|
||||
| `amount` | millisatoshis, stringified | -- | [57](57.md) |
|
||||
| `bolt11` | `bolt11` invoice | -- | [57](57.md) |
|
||||
@@ -286,6 +299,7 @@ They exist to document what may be implemented by [Nostr](https://github.com/nos
|
||||
| `emoji` | shortcode, image URL | -- | [30](30.md) |
|
||||
| `encrypted` | -- | -- | [90](90.md) |
|
||||
| `expiration` | unix timestamp (string) | -- | [40](40.md) |
|
||||
| `file` | full path (string) | -- | [35](35.md) |
|
||||
| `goal` | event id (hex) | relay URL | [75](75.md) |
|
||||
| `image` | image URL | dimensions in pixels | [23](23.md), [52](52.md), [58](58.md) |
|
||||
| `imeta` | inline metadata | -- | [92](92.md) |
|
||||
@@ -304,6 +318,7 @@ They exist to document what may be implemented by [Nostr](https://github.com/nos
|
||||
| `summary` | summary | -- | [23](23.md), [52](52.md) |
|
||||
| `thumb` | badge thumbnail | dimensions in pixels | [58](58.md) |
|
||||
| `title` | article title | -- | [23](23.md) |
|
||||
| `tracker` | torrent tracker URL | -- | [35](35.md) |
|
||||
| `web` | webpage URL | -- | [34](34.md) |
|
||||
| `zap` | pubkey (hex), relay URL | weight | [57](57.md) |
|
||||
|
||||
|
||||
Reference in New Issue
Block a user